Some organizations are winning individual battles for enterprise security—but the bad guys are still winning the war.
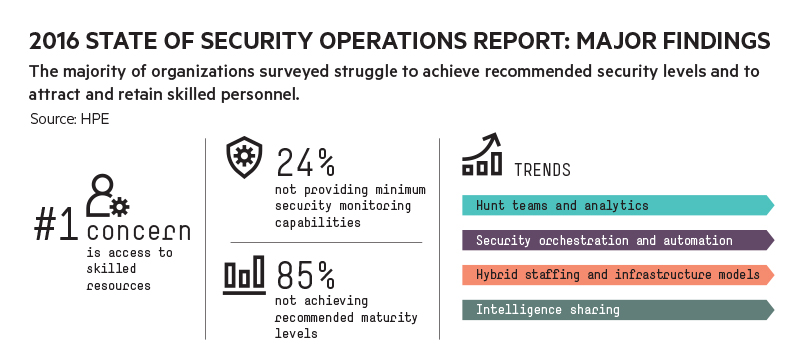
That's the not-so-great news from HPE’s 2016 State of Security Operations report. Although there is a rising tide of advanced security units that fully recognize the business impacts of a breach and employ highly sophisticated strategies to reduce risks, they remain the exception rather than the rule: 85% of the organizations assessed in our annual report aren't meeting the recommended maturity levels for their security operations.
We as an industry need to do better.
Improvement begins with mastering—or remastering, in some cases—the fundamentals of enterprise security. This may not sound exciting, and that's part of the problem: We're too obsessed with what's new and shiny, especially when it comes to technology, and security operations aren't usually new and shiny.
But getting the fundamentals right is an absolute must. Immature security organizations are typically lacking in one or more areas. In some cases, organizations are even trying to implement more advanced strategies without the basics already in place, which is a setup for failure.
For example, a company may hire and deploy an advanced hunt team within its security operations center (SOC)—a rising trend, according to the report—but neglect to do traditional monitoring, sometimes as a shortcut for managing budget constraints. As we note in the report: "These organizations are not reaching minimum security capabilities, and are operating without any real-time monitoring abilities."
Mastering the basics
Here are my recommendations for putting in place enterprise security fundamentals:
- Document your processes and procedures. We continue to see far too many organizations that run their security operations with little or no documentation around processes and procedures. According to the report, one in four security organizations operates on an ad hoc basis, with little or no documentation. We saw a real-world example of this recently at a retail business. It suffered a brain drain every time someone left the company—and even when shifts changed in its SOC—because of a complete lack of documentation. The security strategy was essentially "do your best." By taking the very tangible step of documenting its knowledge and processes, the business was able to raise its security maturity scores for both its “processes and procedures” and its “people” categories, because employee retention improved as a result of this change.
- Create clear use cases. Many SOCs also lack use cases that define their actions and processes. A use case helps staffers react to situations. For example, if event “X” happens, this job role (or set of roles) responds by taking these “Y” steps. Use cases need to be specific: "Monitor traffic" is a bad use case, because it's vague and asks analysts to comb through mounds of data with no clear goal. "Monitor for users trying to escalate their privileges" is a good use case that will lead to a tangible outcome.
- Define what success looks like. Too many well-intentioned enterprise security groups set out with ambitious plans for combating the latest threats and improving their corporate posture. Yet they have no metrics for measuring whether their efforts are successful. A SOC statistic we love, for example, is events per analyst hour. This shows what the analyst is actually doing for the organization, unlike simply tracking events per hour or incidents per hour, which don't reveal anything about effectiveness.
- Make use of the wealth of information out there. You're off to a good start: You're reading this article! But don't stop here. There's a ton of great security information and advice out there, and much of it is free—make use of it. The bad guys gain an edge by constantly sharing and acting on information. The security industry must do the same. We're seeing mature security organizations prioritize information sharing with one another.
- Optimize what you already have. Struggling security organizations often aren't making full use of the technology assets they already have. For instance, ArcSight ESM has right-click integration. This can be configured to allow an analyst who sees an attack on an IP to simply right-click and disable traffic to that machine for 24 hours, yet I have only seen one customer using this capability to resolve this type of attack. This gets back to our love of "new and shiny": There's no point in chasing the latest and greatest if you don't make full use of what you already have in place.
Optimizing and advancing your strategies
Once you've mastered the basics, you can begin to learn and adopt the strategies that leading organizations are using today:
- Re-examine security's place in the organization. Maturing security organizations are getting out of the "entrenched-in-IT" mindset and becoming more plugged in to the overall business, eliminating conflicts of interest and responsibilities in the process. Similarly, we’re seeing more CSOs/CISOs come from business rather than technical backgrounds. Some security organizations are moving out of IT and into the governance, risk, and compliance (GRC) division, which may help draw a clearer connection between security budgets and the potential financial costs of a breach.
- New staffing strategies. The right people are as necessary as the right processes and technologies, and access to skilled resources remains the number one concern among CSOs and CISOs. As a result, more organizations are exploring hybrid staffing models: They still run their SOC, but they may rely on external resources for Level 1 monitoring or off-hours support while retaining Level 2 analysis and incident response internally—as well as full visibility and ownership of their security data.
- Big data analytics. Mature organizations don't just flood the SOC with data. They create good use cases and make sure that the data flowing to the SOC is useful, which in turn makes the SOC more successful, because people know how to handle the data that’s coming to them and aren’t digging through a ton of noise. Using advanced analytics in conjunction with a hunt team is a rising trend in mature organizations.
- Orchestration and automation tools. We're seeing growing adoption of orchestration and automation in the SOC in areas such as incident response—in part as another strategy for overcoming staffing challenges and reducing the burden of coping with lower-tier events.
- Security maturity isn't just about keeping up with the bad guys. It's about enabling the business for bottom-line success and minimizing risk in the process. If your organization has been struggling, rest assured that it doesn't have to always be an uphill climb. Improvement is absolutely achievable. Start with the basics, and you'll have a rock-solid foundation for the more advanced security strategies needed for the modern threat landscape.
Keep learning
Learn from your SecOps peers with TechBeacon's State of SecOps 2021 Guide. Plus: Download the CyberRes 2021 State of Security Operations.
Get a handle on SecOps tooling with TechBeacon's Guide, which includes the GigaOm Radar for SIEM.
The future is security as code. Find out how DevSecOps gets you there with TechBeacon's Guide. Plus: See the SANS DevSecOps survey report for key insights for practitioners.
Get up to speed on cyber resilience with TechBeacon's Guide. Plus: Take the Cyber Resilience Assessment.
Put it all into action with TechBeacon's Guide to a Modern Security Operations Center.