Next week, thousands of people in the information security industry will be in San Francisco for the RSA Conference, where they will hear about the latest industry trends and see products that implement them. And there is bound to be some interesting developments around encryption that will be part of this.
It will be good to see how new encryption products fit into the evolution of the technology that has proceeded over the past couple of decades. That's roughly how long it has been since the dot-com boom kick-started the business use of the Internet. It's also when the increase in cyber-crime started that drove the widespread adoption of encryption.
Back in the dot-com era, there was essentially one encryption technology that was commonly used—the Secure Sockets Layer (SSL) protocol that is used to create secure sessions with web servers. It was eventually upgraded to the Transport Layer Security (TLS) protocol that is more commonly used today. The Shodan search engine estimates that over 12 million servers are currently protected with SSL or TLS, almost certainly making them the most successful applications of encryption ever invented.
There was not much interest in other encryption technologies at the time. This might have been because cyber-crime was very uncommon, at least by today’s standards. It was so infrequent that the Internet was much like the fictional town of Mayberry, North Carolina, where Sheriff Andy Taylor spent more time tasting pie at the county fair than on actual law enforcement.
This was reflected in the American Bar Association’s (ABA) Formal Opinion Number 99-413 (March 10, 1999), “Protecting the Confidentiality of Unencrypted E-Mail,” which told lawyers that it was okay to use unencrypted email for sensitive communication with clients. Their reasoning was roughly that the chances of the email being intercepted were low and intercepting email was illegal, so that users of email had a reasonable expectation of privacy when using it.
Today, however, things are very different. The world has become a much more dangerous place. It's now one in which the modest threat from casual hackers has been replaced by the serious threat of attacks carried out by well-organized, for-profit cyber-criminals.
The latest guidance from the ABA, Formal Opinion 477R (PDF) (May 22, 2017), “Securing Communication of Protected Client Information,” has even been updated to reflect this new reality. It no longer assumes that unencrypted email communications will necessarily provide a reasonable expectation of privacy.
Similarly, many laws and regulations now provide strong incentives for using encryption to protect sensitive information: the Health Insurance Portability and Accountability Act (HIPAA), Payment Card Industry Data Security Standard (PCI DSS), General Data Protection Regulation (GDPR), and California Consumer Privacy Act (CCPA) all do this. Many similar data-protection laws and regulations are in the works. And while regulatory compliance has driven the adoption of encryption by businesses, encryption technology has also evolved.
Here's a look at the state of encryption ahead of this year's RSA Conference, and a call to action.
The evolution of encryption
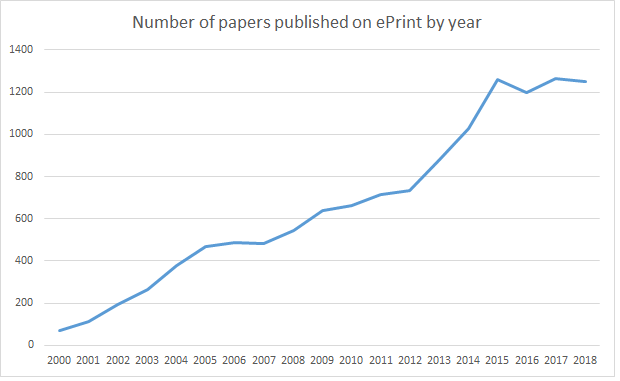
There have been many innovations in encryption technology since the dot-com boom. The number of academic papers that have been published on the topic is a good measure of this. Figure 1 shows how the number of encryption papers has exploded over the past several years, as measured by the number of papers posted to the ePrint preprint server for the International Association for Cryptographic Research (IACR).
Figure 1. Numbers of papers published on the IACR preprint server by year.
And although it looks as if the amount of research in encryption has boomed in the recent years, it also looks as if very little of this research contains ideas that are worthy of being implemented. A small fraction, probably less than 0.1%, of these ideas ever see commercial use. Those that have done this seem to have a couple of common elements in common: They either make encryption cheaper and easier to use, or they provide useful capabilities that were previously unavailable.
[ Special Coverage: RSA Conference 2019 ]
Encryption, now shipping
Examples of technologies that make encryption cheaper to use include identity-based encryption (IBE) and format-preserving encryption (FPE). Technologies that provide additional useful capabilities include order-preserving encryption (OPE) and fully homomorphic encryption (FHE). All of these are available in shipping commercial products.
Two of these have even achieved a level of recognition by standards bodies. There are ISO (ISO/IEC 18033-5:2015), IEEE (IEEE Std 1363-3:2013) and IETF (RFC 5091, RFC 5408, RFC 5409) standards for forms of IBE, and NIST has approved a form of FPE (SP 800-38G) for use under FIPS 140-2, its Security Requirements for Cryptographic Modules standard. Standards for OPE and FHE have not appeared yet, perhaps because the technologies are still relatively new, but they will almost certainly follow if the technologies become widely used.
IBE provides a way to calculate users’ public and private keys as needed as an alternative to generating them randomly. This means that expensive secure key archiving and key distribution are unnecessary, which makes the technology cheaper to buy, use and support relative to alternatives.
FPE provides a way to encrypt data that keeps its format compatible with existing IT environments. This makes it cheaper and easier to use encryption in systems that have legacy components that are either hard or impossible to modify to handle encrypted data that has a different format than its unencrypted counterpart does—an application that expects a credit card number to comprise 16 decimal digits may fail if given an encrypted value that looks like little more than 128 random bits.
OPE provides a way to search and sort data without having to decrypt it. FHE provides a way to perform calculations on encrypted data without having to decrypt it. Both of these look promising in cloud applications.
Having cryptographic keys in the cloud probably isn't secure, and it can be prohibitively expensive to move data from the cloud to a secure location. Thus, being able to do useful operations on encrypted data is very useful, and both OPE and FHE provide a tool that lets you do this.
The rise of cyber-crime should increase adoption
None of these technologies existed in the dot-com era. Yet all of these technologies are available today in generally available commercial products, and their development seems to be driven by the need to provide additional protection to sensitive data against the increased threat of cyber-crime.
At this year’s RSA Conference, expect to see innovations that keep decreasing the cost of encryption by making it cheaper to buy, use, and support. And expect to see innovations that provide additional useful capabilities that were previously unavailable. Innovations like these have kept coming for the past 20 years and there is no reason to expect for this to stop any time soon.
Let’s just hope that we start seeing more than 0.1% of research that leads to practical solutions. An increase to even 1% would provide lots of ways to protect the sensitive data that cyber-criminals use to commit the billions of dollars of fraud that we currently suffer.
For more on the state of cryptography, drop in on The Cryptographer's Panel on March 5 at 9:20 AM at the RSA Conference, which takes place March 4-8 in in San Francisco.
Keep learning
Get up to speed on unstructured data security with TechBeacon's Guide. Plus: Get the Forrester Wave for Unstructured Data Security Flatforms, Q2 2021.
Join this discussion about how to break the Ground Hog Day repetition with better data management capabilities.
Learn how to accelerate your analytics securely into the cloud in this Webinar.
Find out more about cloud security and privacy, and selecting the right encryption and key management in TechBeacon's Guide.
Learn to appreciate the art of data protection and go behind the privacy shield in this Webinar.
Dive into the new laws with TechBeacon's guide to GDPR and CCPA.