A digital product is only as secure as its weakest link, and software is increasingly under attack. To address this, organizations need to take a holistic approach, which includes value stream management, to protect their entire software supply chain. This addresses products from both commercial and open-source third parties, any in-house software, and your software factory.
The problem requires urgent attention. Over the last couple of years, the industry has faced a steep increase in security attacks on digital products and services. Last year there was a 650% increase in software supply chain attacks, aimed at exploiting weaknesses in upstream open source ecosystems, according to the 2021 State of the Software Supply Chain report.
As a result of the attacks and to strengthen US cybersecurity posture, in May 2021 President Joseph Biden signed an Executive Order that mandates cybersecurity standards and requirements for any vendor that conducts business with the federal government, including the requirement from vendors to provide a software bill of materials.
My company, Micro Focus, has successfully implemented a holistic approach to security, and you can also. Here's what we did, and what you need to know.
How the software supply chain works
The supply chain consists of activities taken by the organization to transform resources and materials to deliver a product or service to the customer. This is akin to other industries such as manufacturing, where the supply chain concept originated. In software that means transforming the code, artifacts, tools, and infrastructure into a delivered software product and/or a runtime service.
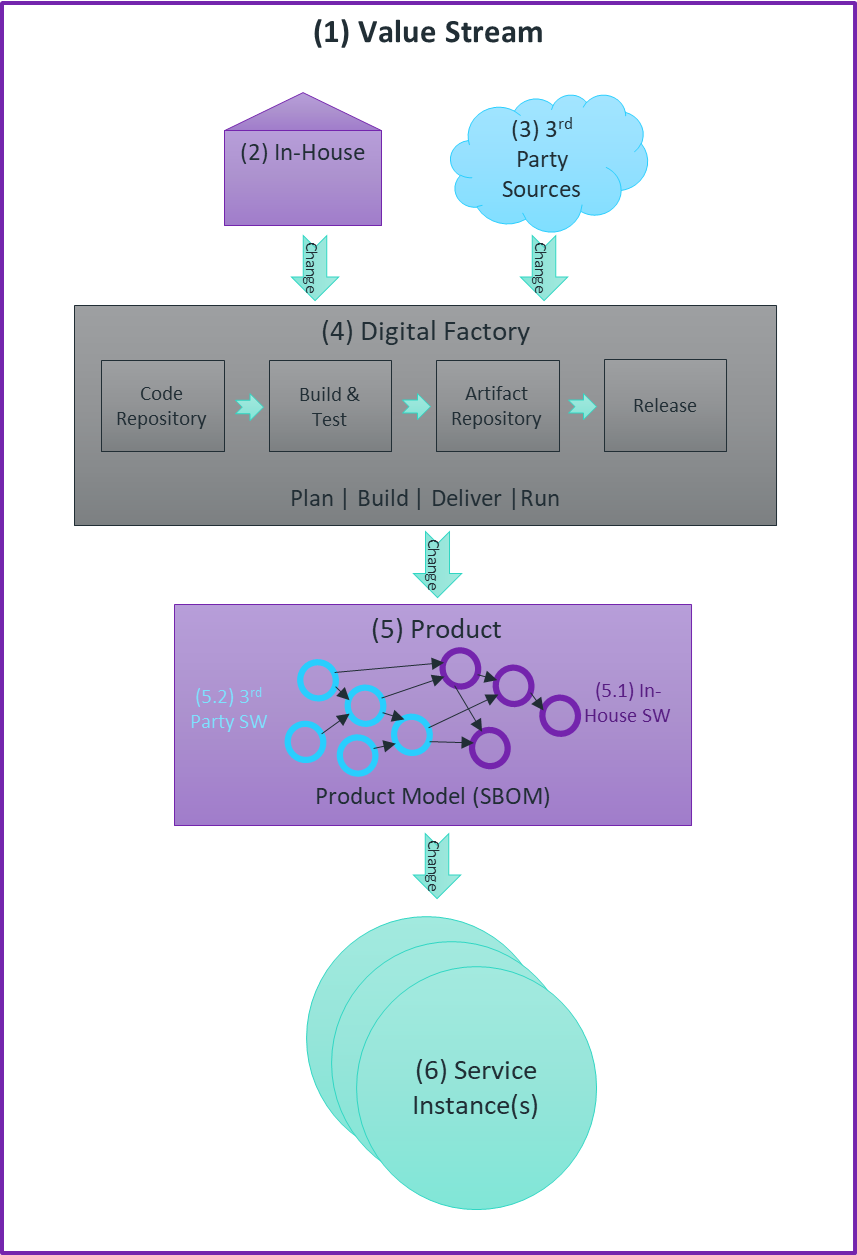
A typical software supply chain is illustrated in Figure 1, below. Changes flow through the (1) value stream to translate customers’ needs into customer value. These changes can be fulfilled (2) in-house, such as by the IT department as well as (3) pulled from third-party sources.
These changes will go downstream through the (4) digital factory, get into the organization's code repository, trigger a build and test cycles, and output a product artifact. That artifact (5) includes both (5.1) in-house and (5.2) third-party sources. These changes can span infrastructure, application business logic, operational procedures, etc.
The product can be run as a (6) service instance and/or the artifact can be delivered downstream to customers and become part of their upstream supply chain.
Figure 1. A typical value stream. Source: Yaniv Sayers
An all-inclusive methodology
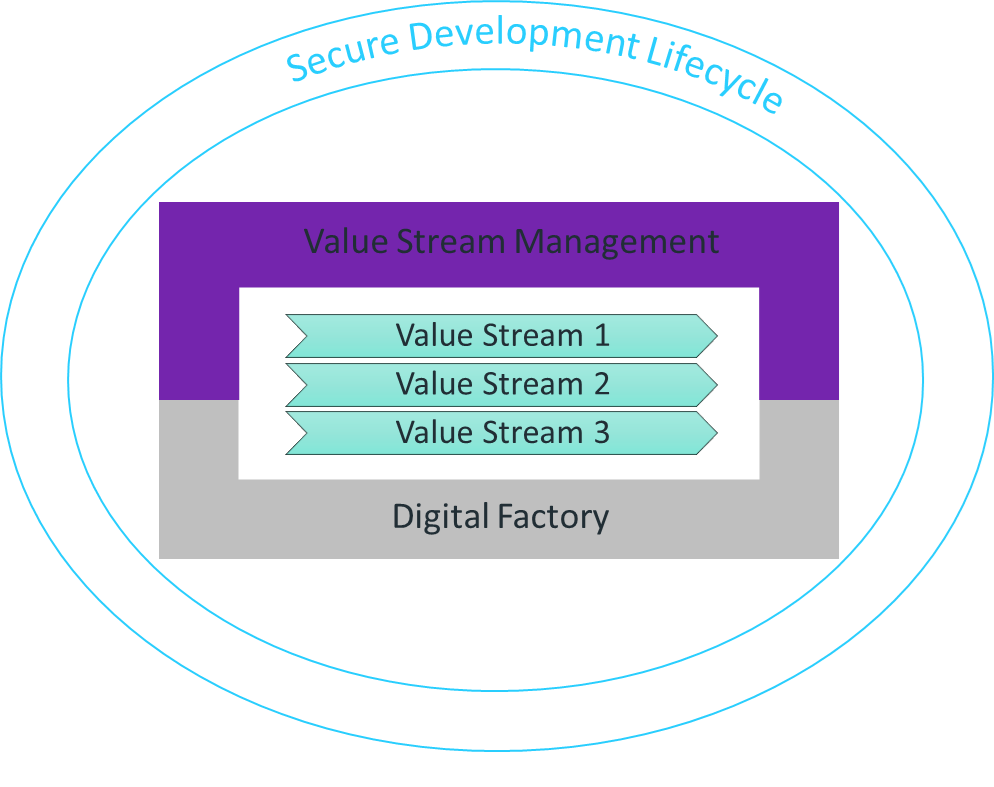
At Micro Focus we've implemented a holistic approach that helps proactively detect, and quickly evaluate and remediate, vulnerabilities. It is based on three main aspects, as depicted in Figure 2, below:
- Secure Development Lifecycle (SDL) Framework: Adapting best security practices to our own products and business processes
- Value Stream Management (VSM): Providing governance, insights, and traceability across the supply chain
- Digital Factory: Underpinning the value stream delivery platform, composed of an integrated set of practices, processes, services, and tools that we use to plan, build, deliver, and run digital products and services
Figure 2. Micro Focus' holistic approach. Source: Yaniv Sayers
Our Secure Development Lifecycle Framework
After adopting the security industry's best practices, we adapted them to our own products and business processes. We then established secure software design and coding techniques and implemented our comprehensive Secure Development Lifecycle framework to support end-to-end secure development and shipment.
This incorporates several security layers in our development lifecycle, allowing us to include security from the early development stage to a proactive test of the security controls' efficiency as development moves on. Security experts provide static code analysis and hands-on security penetration testing.
Value stream management
We implemented VSM to maximize business outcomes and effectiveness by aligning our business strategy with software delivery, and to maximize efficiencies by detecting and removing waste and friction.
The VSM solution underpins our security and quality-governance management. All information—including backlog items, requirements, tests and test results, vulnerabilities, and so on—are captured and audited. The system provides insights and visibility about quality and security status.
This allows stakeholders to make informed decisions about where the risk areas are, which actions should be taken to address any problems, and whether a release can be deployed to production, among other things.
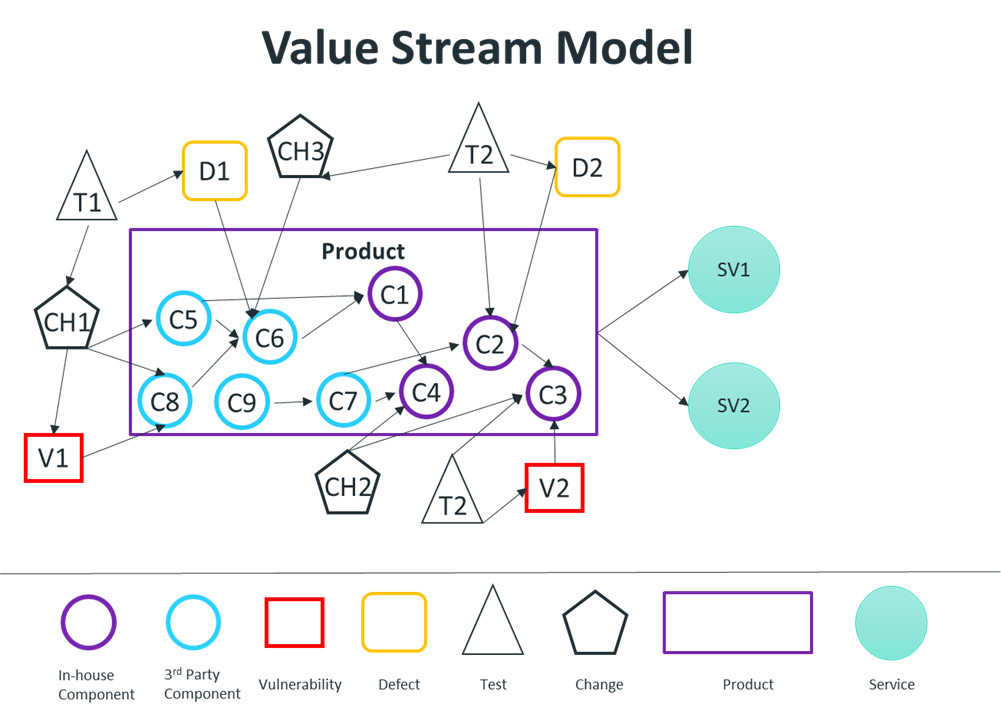
This also provides traceability for the complete flow of changes through a unified value stream model, such as what you see in Figure 3. The model contains a representation of all the product components (in-house, third-party, open source and commercial) and their interdependencies, i.e.. exactly what is needed for a Software Bill of Materials (SBOM).
In addition, the model provides traceability between the end product and all the value stream artifacts including changes, tests, defects, vulnerabilities, environments, etc. The model takes into consideration that each product may have different versions that may run in various service instances and environments.
Figure 3. A unified value stream model. Source: Yaniv Sayers
Through this model we can quickly analyze which products and service instances may be impacted by a known vulnerability and to what extent, get visibility about outdated versions or at-risk third-party components that need to be updated, alert the respective owners that need to act for each component, and take other actions.
We initially mapped the value stream, realizing that each of the links can be potentially breached—thus we have to capture all possible attack vectors. All the activities, roles, systems, and data involved span from upstream third-party and in-house sources to the downstream product delivery.
We mapped all the different third-party sources, who pulls them and how they are pulled, where are the artifacts stored, how the change flows through our software factory, and how the change is eventually delivered into the product.
We are a large-scale enterprise, with more than 50,000 different third-party components, which isn't uncommon for enterprise organizations. With that in mind, we need an enterprise-ready solution to provide end-to-end visibility and traceability across the value stream and over the complete product model, so we can take proactive measures to govern and secure our products and services.
The comprehensive value stream model delivers many other benefits:
- Compliancy management: Through the model we can quickly get visibility for every third-party license and validate compliancy. In addition, the model automatically generates a SBOM that includes direct third-party dependencies and transitive dependencies. Unless automated, this would have required a huge amount of effort to be defined manually for every release and likely include many human errors.
- Quality management: Like with security, product quality should be evaluated holistically including its in-house and third-party dependencies. Through the model we can understand the overall product quality, identify components with lower quality or lower coverage, take corrective actions, and eventually deliver software with higher confidence.
- Cost management: Through the model we can get an understanding of the complete product and/or service total cost of ownership, including its in-house and third-party components, tooling, infrastructure, and so on.
- Environmental impact analysis: There is an increasing emphasis on minimizing environmental impact (e.g. carbon footprint). The model measures the complete product and service environmental impact.
- Value analysis: Changes flow to fulfill business objectives, whether it is to improve customer satisfaction, increase renewal rate, or accomplish other goals. The value stream model can help you realize if the delivered changes align with the business objectives and evaluate return on investment.
Our digital factory
The digital factory underpins the value stream delivery platform. It comprises an integrated set of practices, processes, services, and tools that lets you plan, build, deliver and run digital products and services. The factory follows the same Secure Development Lifecycle policies and practices that the individual products do, including threat modeling, security reviews. It also automates the SDL and delivers shared security services such as security test automation services.
Securing the digital factory itself
Based on the value stream mapping outcome, we have gone through every step and activity: The source code management system, the build environment, the artifact repository, and so on. For each we analyzed the different threat vectors, prioritized the findings, and implemented a remediation action plan.
Every change in the factory goes through this type of security review and assessment to protect the factory from hackers infiltrating into it and injecting malware.
Vetting third parties
Every third-party component follows a vetting process to detect security and license risks before it is approved for use. This includes the following steps:
- Making sure that the software license agreement meets our requirements, such as time to respond for critical security incidents
- Taking it through a security and malware scan, looking for known vulnerabilities
- Confirming who sponsors it and how popular it is in the community
- Looking at how well and how quickly prior vulnerabilities were addressed
Securing third-party software is essential to our process; approved third parties are added to an in-house trusted repository.
Shift left and continuous validation
We take a shift left and continuous testing and validation approach across the lifecycle. This allows us to be proactive, detect early, and reduce risk as we transition to production. We are basically accelerating flow with DevSecOps and the software factory. The factory provides a spectrum of security services, including static code analysis, dynamic code analysis, third-party dependency validation, scanning infrastructure and infrastructure-as-code, container validation, malware scanning, penetration testing, code signing, and others.
The services are integrated across the delivery pipeline and are addressed as early as possible. This means, for example, we execute continuous security testing over the source code repository to detect vulnerabilities in the development branch. Once a code change is committed, dynamic security and third-party scans are run.
As the change progresses, additional guardrails will be executed, including penetration testing, proactive monitoring, and continuous change management for the latest security patches.
We also use a similar shift-left approach for functional and performance validation. We address validation as early as possible with faster cycles; as the build is promoted, we execute additional guardrails to reduce risk.
We use a mature formal process to handle vulnerabilities that are identified both internally and externally. We have a robust, dedicated, full-time threat intelligence team with an enterprise-wide view. This team constantly reviews new reports of vulnerabilities, threats, and compromises for possible impact to our products and network.
Follow the model
Using the VSM product model, we can quickly analyze impact and take any required actions, and through the digital factory's automated delivery pipeline we can quickly remediate our products and services. For example, with the recent Log4Shell vulnerability, we immediately realized the impact on our products, remediated the vulnerability across those products to protect both SaaS and on-premises customers, and issued security bulletins with instructions on how to remediate for on-premises installations.
While digital transformation is driving every company to become a software company, it also means that every company—including traditional industries such as manufacturing, utilities, pharmaceutical, governments, and others—is becoming more exposed to software security attacks. Add to this the shift to everything-as-code, and there is a fertile soil for hackers to expand their attack surface.
These threats require a holistic approach, such as what we at Micro Focus have adopted. It's not necessarily a quick fix, but it works for us—and it can for you, too.
Keep learning
The future is security as code. Find out how DevSecOps gets you there with TechBeacon's Guide. Plus: See the SANS DevSecOps survey report for key insights for practitioners.
Get up to speed fast on the state of app sec testing with TechBeacon's Guide. Plus: Get Gartner's 2021 Magic Quadrant for AST.
Get a handle on the app sec tools landscape with TechBeacon's Guide to Application Security Tools 2021.
Download the free The Forrester Wave for Static Application Security Testing. Plus: Learn how a SAST-DAST combo can boost your security in this Webinar.
Understand the five reasons why API security needs access management.
Learn how to build an app sec strategy for the next decade, and spend a day in the life of an application security developer.
Build a modern app sec foundation with TechBeacon's Guide.