To manage the complex mix of technologies, vendors, protocols, and topologies that make up enterprise networks today, you need a comprehensive, across-the-board awareness of the compliance issues. Security is a critical subset of compliance and a critical factor in networks, since the network is the doorway to the company jewels—its data.
Unfortunately, most efforts to establish and maintain security compliance continue to lag behind the many vulnerabilities that threaten these networks. Most attacks exploit known vulnerabilities that have never been patched, despite the fact that patches had been available for months, or even years, before the attack. Understaffing, untrained staff, operational silos, and a lack of effective tools and processes lead to failure. A 3-D approach to compliance can help you get a handle on the problem.
A holistic view considers all the dimensions for network attack vectors. Too often, individual teams work to ensure that their own area is secure and compliant without considering the implications for the larger organizational structure. That sort of siloed thinking is a hacker’s best friend.
Here's what your team needs to know about 3-D compliance, and how to put it to work.
The 3-D compliance model
Like much in IT operations management, network compliance is a moving target. My team developed a three-dimensional approach that includes the operating system software, the configuration, and the running state of the device.
Many network engineering teams don’t factor in what is happening on the device in real time and fail to consider that this third dimension could leave their networks open to vulnerabilities that can result in data loss and potential penalties.
By monitoring the running state of networked devices and comparing that to the policies defined in the configurations, your networking team can uncover vulnerabilities before they're published in the Common Vulnerabilities and Exposures database of known vulnerabilities. Once you know something is an issue, and it's been confirmed by the vendor, you can alert users to the severity and protect them with a fix, so they can automatically roll back to the baseline.
Networking teams need to improve their efforts to establish and maintain compliance, which unfortunately often lags the vulnerabilities that threaten their networks. The challenge is like the proverbial fox chasing the rabbit around the racetrack: You’re always trying to keep up, and you need to have the best tools and techniques possible to avoid falling behind.
Here's an example of how 3-D compliance can address a current CVE.
3-D in action: Tracking Cisco CVE-2018-0171
To understand the complex relationships of the three dimensions of network compliance, consider a recently discovered vulnerability affecting many Cisco devices. The Cisco Common Vulnerability Exposure CVE-2018-0171, which Cisco acknowledged on March 28, had a NIST/NVD severity of 9.8 out of 10.
The issue is that Cisco's Smart Install, enabled by default on some Cisco devices, unintentionally creates a hole for unauthorized access to the device through an unsecured port. Smart Install is not something you would find in the configurations for these devices, but it's a tool that network engineers commonly use to simplify their work.
To see if Smart Install is enabled, you must use the running state show commands. Unfortunately, in a hectic work environment, cleaning up after priority tasks often gets skipped. In this case, that means a vulnerability would be left open. (Read more about the Cisco CVE here.)
The consequences of an unaddressed CVE
An open port could allow an attacker to insert malicious code into the device. In this case, it would cause an indefinite loop to run, essentially creating a distributed denial-of-service (DDoS) attack on the affected device.
This vulnerability also allows hackers to reconfigure networking devices in ways that don’t immediately cause concern. A device may appear symptom-free, with no negative symptoms that would normally trigger an alert to network administrators. But it leaves a door open for a later attack, such as accessing servers that host databases containing confidential information.
Once you know the criteria defining the vulnerability and create the policy, you can identify vulnerable devices automatically and remediate the vulnerabilities either by way of an automated configuration change or through an operating system update.
Organizations must be able to close the CVE within their networks, and each company has different response protocols for dealing with that. Administrators have two ways they can go here:
- Rely on the network vendor to identify and close the issue on the device with a patch. This takes time, which leaves you vulnerable.
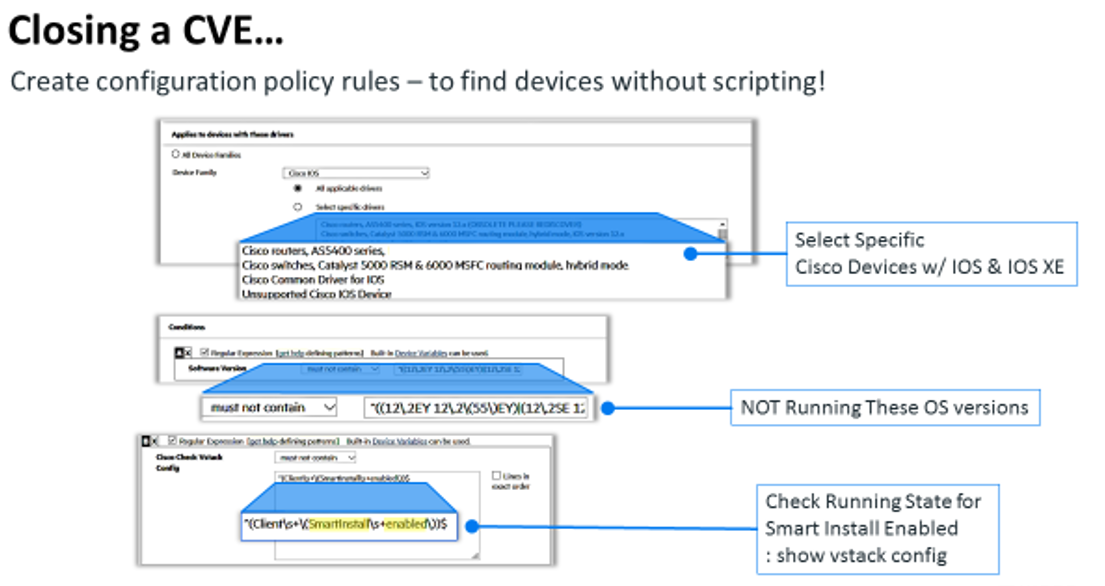
- Add your company-specific configuration rules to what the vendor recommends to reflect your own unique network needs—assuming you have the ability to add those rules. This process might include using your own compliance policy to check the running state to see if Smart Install is enabled. This is a critical option for networking teams that need to close a vulnerability as fast as possible. Triage is an important element in every network engineer’s capabilities.
Don't forget to maintain network compliance over time
In working to close down Cisco CVE-2018-0171, our team learned an important lesson. Often, the complexity required to create scripts, or to close down CVEs manually, leads to only partially compliant fixes.
Here is a simple, powerful way to construct the logic required for this CVE.
 What you need is a way to:
What you need is a way to:
- Find only the affected devices by vendor, model, OS, and running state configuration. (In this case the vstack variable is the key to whether Smart Install is enabled; the “show vstack cmd gives you this status.)
- Run the fix manually or schedule it to execute later.
- Record the history of affected devices and when they became compliant. This is critical for audit reports.
In this example, network engineers who decide to keep Smart Install on their devices for future use may use the “no vstack” command to temporarily disable it. But should someone subsequently enable it manually, Smart Install would remain enabled after the user logs out of the device—unless the user remembers to disable it beforehand.
To completely deal with this CVE, then, you must continually monitor for its reappearance, and then automatically close it. This is a critical element in the compliance lifecycle, which is an ongoing process, not just a single event.
Integrate 3-D into your compliance lifecycle
Since networks are always changing, the job of maintaining compliance is ongoing. It takes a broad and deep understanding of your network, as well as continuous maintenance of your network configuration.
Here is the compliance lifecycle:
Build and deploy policy for configuration, running state, and software version. This is the baseline to maintain, and it includes the elements of 3-D compliance.
Monitor and notify. Perform continuous, real-time monitoring of changes to all three axes, and notify those responsible to screen changes (typically IT operations management).
Check according to policies. Check changes against defined policies and alert engineering and/or security operations of the severity level. Be sure this includes checks on the running state.
Remediate. Restore your baseline quickly and automatically if possible. For new CVEs, check for vendor fixes, and create a new policy if required.
Audit. Create audit reports to maintain a record of all changes.
Now step up to 3-D
Don't focus on just one dimension of compliance at a time. Take a 3-D approach that examines all three dimensions of network operations that includes the operating software, configuration, and running state at any given moment. Follow this model and you will defend your network against the many vulnerabilities that can result in data loss, downtime, and penalties for noncompliance.
With a 3-D approach to network compliance, you'll view network security holistically. And make sure you equip your team with the right tools and techniques to help them understand the full set of dependencies when making networks secure and compliant. This is especially critical for any organization that transitions to software-defined and virtual network technologies, where changes are easy and can propagate rapidly to multiple elements in your network.
Keep learning
Choose the right ESM tool for your needs. Get up to speed with the our Buyer's Guide to Enterprise Service Management Tools
What will the next generation of enterprise service management tools look like? TechBeacon's Guide to Optimizing Enterprise Service Management offers the insights.
Discover more about IT Operations Monitoring with TechBeacon's Guide.
What's the best way to get your robotic process automation project off the ground? Find out how to choose the right tools—and the right project.
Ready to advance up the IT career ladder? TechBeacon's Careers Topic Center provides expert advice you need to prepare for your next move.