According to a recent study by Dimensional Research, a majority of companies interested in software-defined networking (SDN) have either already begun deployment or have fully deployed it for at least a portion of their networks.
That's not surprising: SDN gives you consolidated, programmatic management over a growing host of switches and routers, as well as the promise of a more dynamic and secure network. At least that's the vision. But those business benefits won't come without an investment in additional technologies to manage them.
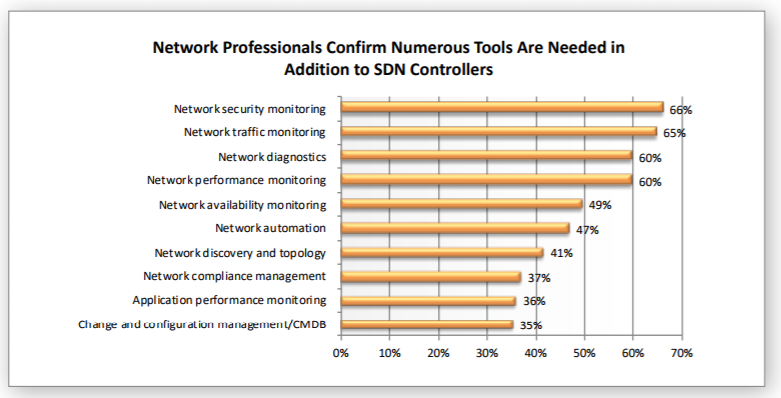
What's missing in SDN
In its survey of 302 network professionals and IT strategists, Dimensional Research reported that respondents want a unified network management system that can handle a mix of SDN and traditional networks. They also want to see security, traffic, diagnostics, and other functionality in their management toolboxes.
Unfortunately, many SDN controllers lack full SDN management capabilities, and they cannot be used to manage heterogeneous networks that include competing vendors’ SDN fabrics.
Most respondents (88%) said they prefer to use SDN controllers from multiple vendors, especially Cisco, VMware, and Microsoft. And such heterogeneous networking environments make management difficult. A unified management console remains elusive.
Why multi-vendor SDN networks?
“While the general SDN vision of 10 years ago looks different from where we are today, adoption is happening,” says Frank Bonifazi, a manager on the networking products team at Micro Focus, which sponsored the report. "We’re just seeing the initial phase of what SDN can ultimately become,” he adds.
Enterprises are acquiring SDN equipment from multiple vendors because of differentiating capabilities and prices, especially in the software-defined wide-area networking (SD-WAN) market, according to Bonifazi. This added layer of complexity presents the risk of “potentially creating SDN vendor-specific silos of expertise,” the report states.
“What was missing in the early academic vision for SDN was the adoption of a single standard for interoperability,” Bonifazi says. “That may come in the future, but for now SDN looks like a continuation of the familiar multi-vendor model, albeit with new software-centric architectures.”
Mixing it up with traditional network infrastructure
Network managers must cope with a multi-vendor mix in most SDN implementations, a situation that's further complicated by the need to support traditional network infrastructure as well. Most companies that add SDN capability to their networks still need to maintain their traditional networking infrastructure.
Only 21% of respondents reported a requirement for standalone SDN management, while 79% wanted centralized management for both SDN and traditional networking.
What network managers want
Given the list of needs cited by SDN practitioners and prospective practitioners, it may seem surprising that SDN is growing in popularity. Chalk it up to the time- and cost-saving benefits that this style of virtual networking has to offer, as well as the technology's promise for the future.
When asked which capabilities respondents felt will most benefit today’s SDN implementations, network monitoring and diagnostics topped the list of improvements they'd like to see.
Without adequate monitoring, security vulnerabilities can go undetected. Attackers typically focus on opening port addresses, redefining network segments, removing Internet Protocol security (IPSec) from interfaces, and many other things.
“Once the network is compromised, it’s like opening up a door you never intended to open,” says Jim Perkins, technical marketing manager for network operations at Micro Focus. There are many ways networks can be compromised, Perkins, adds, but these generally fall into two camps: either a malicious virus attacking the embedded device operating system, or an out-of-compliance configuration change that creates increased vulnerabilities to the network, or possibly denial-of-service issues.
In addition to monitoring for attacks, the report describes practitioners’ interest in automation: “Automation also provides the opportunity for auto-remediation, creating the opportunity to resolve issues before users are affected and the business is impacted.” Compliance automation is top of mind, says Perkins.
“Keeping your network in compliance is a difficult job if you’re not using monitoring and automation tools to keep up,” he says. “For example, you need to keep device OSes and policy-compliant configurations stored and ready for remediation on one or more devices. This can be done automatically without any human interaction.”
Some SDN standards still evolving
As with most communications technologies, SDN evolution has seen some vying for control of standards by competing vendors and consortia. The communications protocol OpenFlow, an open-source project that allows control of network switches, is still being used, says Bonifazi. But more is needed to support the multi-vendor SDN environments and mixed networking environments. In some cases, vendors are enabling dual OSes on their SDN elements, but the capabilities are not equal for each, Bonifazi says.
“What we’re seeing is that expert network engineers are required to make OpenFlow work, for example, on these operating systems, beyond simple operation. But most businesses we work with are not looking to be on the bleeding edge of technology, but rather to make the transition to SDN in a low-risk manner, while taking advantage of its inherent value: increased agility, security, and programmability in response to business needs.”
Standards normally reduce the risk in technology adoption, but the battle among vendors to establish control points in the industry continues. “That’s a familiar story. The pressure on all the players to dominate with a single standard reduces the time it takes to provide organizations with what they’re looking for,” says Bonifazi.
Where network operations systems should go next
“Network professionals want more network visibility and the power to automate network deployments, configuration and remediation,” the report concludes. That means more than just having high-level visibility across a unified network of SDN and traditional networks. “It means seeing how things are connected, what protocols are being used where, monitoring for issues, and the reasons for them,” says Bonifazi. “With this accomplished, network operations centers (NOCs) can deliver network services with confidence.”
Beyond that comes the automation capabilities—both for SDN and traditional networks. The advantage of SDN lies in its ability to make rapid, programmatic path selection, trunking, and other networking functions.
But that will require extra provisioning of network infrastructure to make those changes without negatively affecting current network operation. “Automation can be based on human rules, supported by data collection and analysis. Ultimately, however, bots may be able to take actions in place of operators,” Bonifazi says.
Keep learning
Get up to speed fast with TechBeacon's guide to the modern data warehouse.
Download the Buyer's Guide to Data Warehousing in the Cloud.
Get up to speed on digital transformation with TechBeacon's Guide.
How important is digital transformation to your org? Take our survey and find out how you stand next to the competition.
Thinking of making a change? TechBeacon's Careers Topic Center provides expert advice to prepare you your next career move.