Security is one of the most underrated aspects of Android development. We spend a lot of time designing and developing our apps, but hardly any time taking care of security.
Many Android apps store sensitive user data but lack even a basic level of security. A lot of highly popular apps in Play Store are known to have serious loopholes and vulnerabilities that any determined hacker with decent-enough skills can easily exploit in almost no time.
That's why I've compiled this list of useful tools that can analyze your Android apps and tighten their security.
If you are a security researcher who likes playing with different apps and finding their weak spots, then this information can be helpful for you as well. Use these tools to analyze any Android app to look for security loopholes and vulnerabilities that can potentially harm the app's users.
Androguard
Androguard is a powerful and well-maintained reverse-engineering tool for Android that's written in Python. It can give you a lot of control for manipulating the DEX files of your app. It can also help you perform static code analysis and diagnose your app for the presence of malware.
It comes with other useful features such as checking the "diff" of two Android Package Kit (APK) files, measuring the efficiency of various obfuscators (such as ProGuard and DexGuard), and checking if the app under test has been illegally modified or tampered with.
ApkTool
This is another hugely popular and regularly updated reverse-engineering tool for Android. Initially released in 2010, it has changed a lot over time.
You can use this tool to crack open any closed, third-party Android app and convert it to its near-original form, analyze it, and rebuild it with custom modifications. It makes reverse engineering pretty easy with its familiar project-like file structure. It also streamlines and removes the redundant actions that are involved in the reverse-engineering process.
Appknox
Appknox is one of the most comprehensive security testing tools around. It statically analyzes the code binaries for potential security flaws and vulnerabilities in any corner of your app.
Automated testing can help only to a certain extent, so Appknox takes the game to the next level. It uses renowned ethical hackers to manually test your app to find deep security loopholes, sensitive data leakages, and other potential weak points that could be compromised.
CharlesProxy
This powerful and useful tool can help you proxy and debug all sorts of HTTP-related things in your app. It is not specific to Android; it can be used with iOS, too.
CharlesProxy basically sits between your app and the Internet. It can help inspect and even change the way your app talks to the network.
You can take any app, start intercepting, and see the network requests as they happen. This can make testing and diagnosing security flaws easy and convenient. Not only that, but you can also modify the requests that your app makes and test different edge cases.
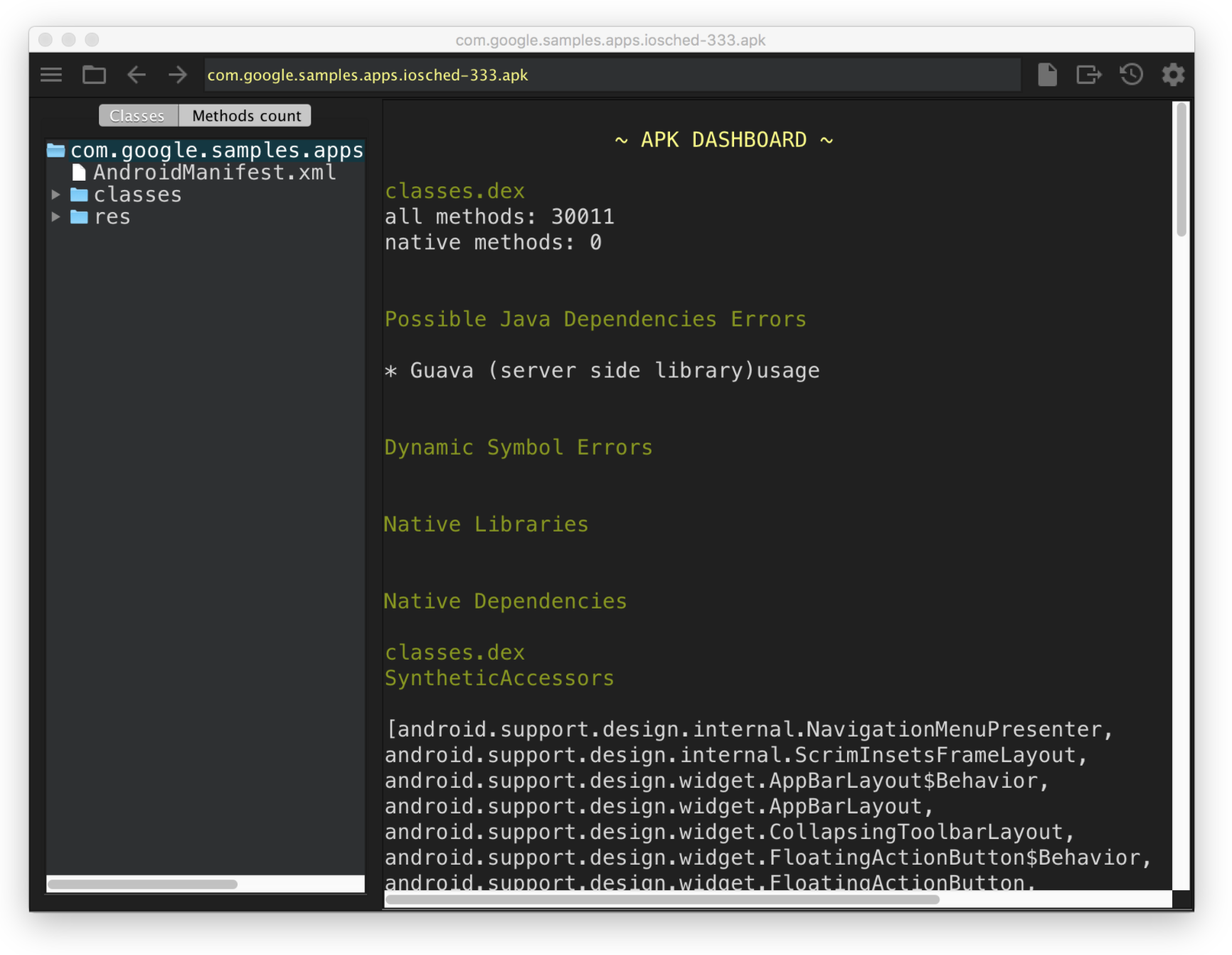
ClassyShark
Figure 1: ClassyShark's APK dashboard
ClassyShark is a simple and easy-to-use binary inspection tool for Android. You can browse all the classes, members, and dependencies and check the method count of any app with ease. I have found ClassyShark to work perfectly with any app I throw at it.
It also has a convenient package-like file structure for easy browsing. And the "Methods Count" tab is a true life-saver that tells you the number of methods each package is contributing to your app.
DeGuard
This is a powerful online tool that uses machine learning to reverse the effects of code obfuscators.. DeGuard leverages the power of artificial intelligence to provide superior reverse engineering.
It has worked really well every time I have given it a try. And the best thing about it is that the more it is used, the better its AI becomes.
DevKnox
This tool can constantly assist a developer in improving the security of code. It auto-corrects several known security issues directly in the IDE while developing the app.
DevKnox works well in Android Studio and understands the context of the code you are writing. It gives you real-time security suggestions and one-click fixes to improve your productivity significantly.
Dex2Jar
Dex2Jar is a popular and well-maintained tool. It packs a lot of useful features for reverse engineering Android apps. For instance, you can use it to easily read and write DEX files, and translate or modify them, too.
You can convert all your DEX files to class files and get them all zipped as a Java Archive (JAR) file format. You can also disassemble DEX files to smali files and assemble them back from smali to DEX again.
DexGuard
It is almost mandatory to pass your Android app through some obfuscator before releasing it. You probably use ProGuard as your default obfuscation tool, and that works just fine. But DexGuard (coming from the makers of ProGuard itself) significantly ups the ante.
DexGuard includes advanced features like class encryption, string encryption (hiding keys becomes super easy now), call hiding with reflection, and native code obfuscation. These can make it difficult for someone to reverse engineer your app. The tool also provides several cool utilities to detect tampered APKs, Xposed Framework, rooted devices, and more.
Drozer
Drozer is a powerful and comprehensive security auditing framework. Auditing your apps and devices with Drozer can give you the confidence that they don't pose any unacceptable security vulnerability or risk.
The tool can also make the Android security assessment really fast and seamless by automating several tedious and time-consuming tasks such as:
- Discovering and interacting with the attack surface exposed by Android apps
- Executing dynamic Java-code on a device, avoiding the need to compile and install small test scripts
- Running regression tests for security issues
- Testing your exposure to public exploits
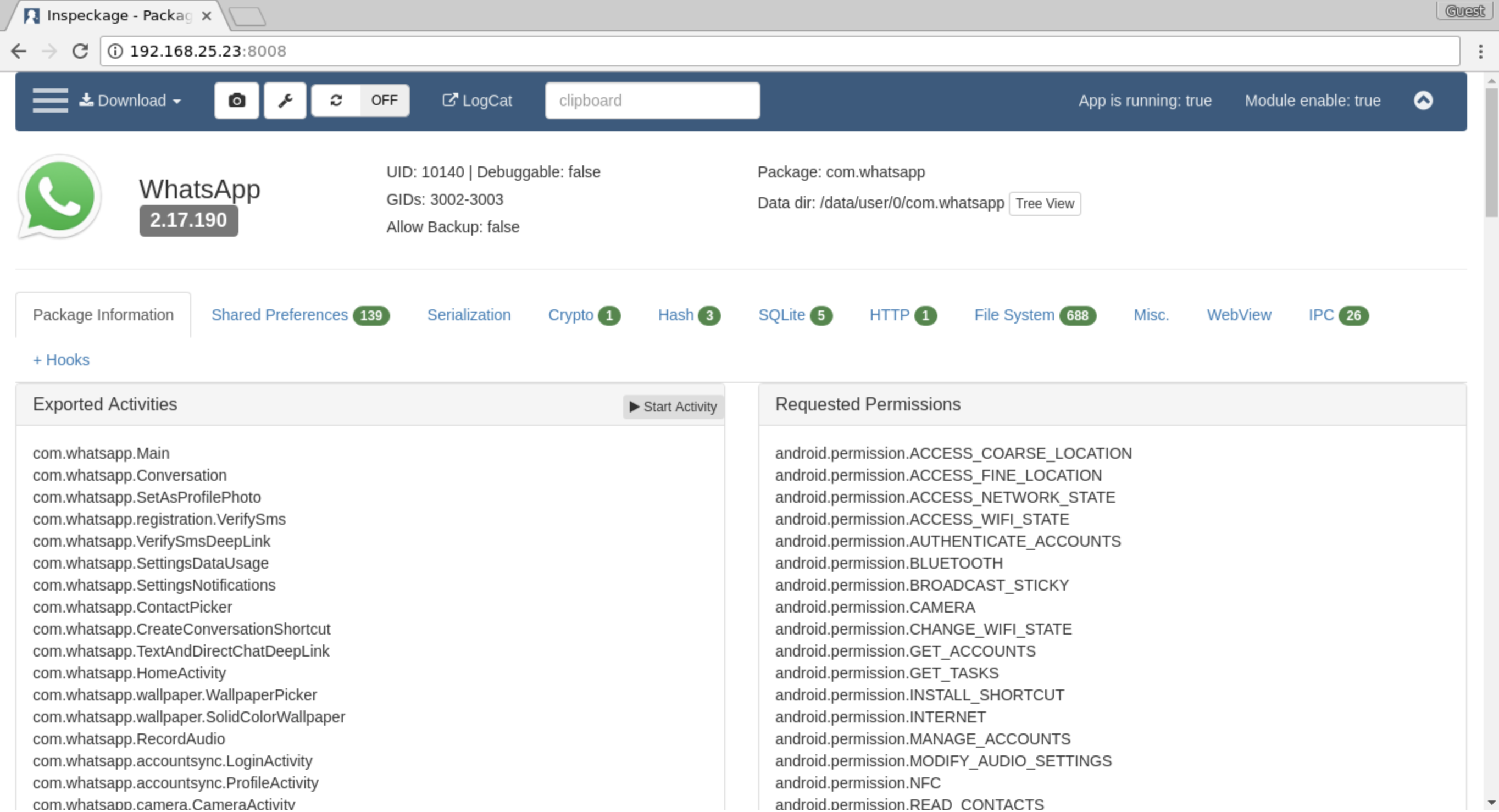
Inspeckage
Figure 2: Inspeckage being used on WhatsApp
Inspeckage is another awesome security testing tool. It comes packed with features that let you perform dynamic analysis (malware analysis or penetration tests) of Android apps by letting you hook into functions of various APIs under test.
It also comes with a built-in web app that lets you perform all actions in a simple and intuitive GUI. The combination of power and simplicity in this tool makes it a must-have.
Intent Sniffer
Intent Sniffer allows you to monitor or spy on any intent (such as starting activities or services) in any Android application. It also lets you dynamically update intent actions and categories at runtime.
This can prove to be useful for testing various data that you want to send from one activity to another, or to services, to discover potential weak points in the application.
QARK
QARK, which stands for Quick Android Review Kit, is a useful security tool, developed by LinkedIn. It helps find common security vulnerabilities not only in the source code but also in the packaged APK of an Android app.
It is easy to use as well, giving you lots of in-depth explanations for the vulnerabilities. QARK's decompilation results are far superior to those from many other decompilers, since it uses multiple decompilers and combines their output for better results.
Tracedroid
Tracedroid is an automated dynamic analysis tool for Android applications. It lets you analyze several aspects of an app under test, such as its network communication, UI interaction, internal code functionality, and others.
To start the automated analysis, all you need to do is upload the APK under test and you are good to go.
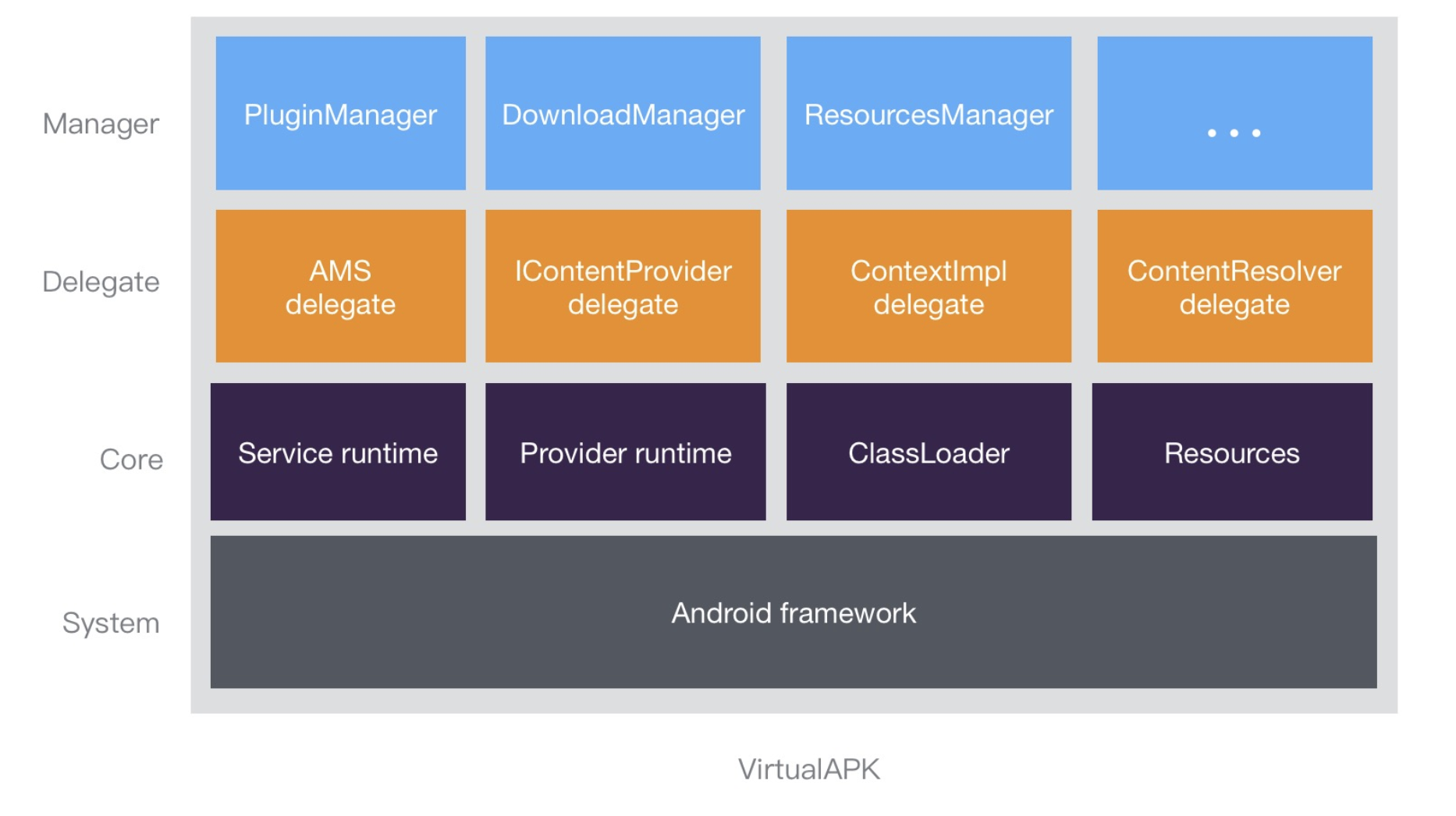
VirtualAPK
Figure 3: Diagram of a VirtualAPK instance
This is a powerful plugin framework for Android that lets you load and run any APK file seamlessly—as if it were an app installed right on your device. This can make analysis a lot easier by allowing you to access any activity, service, receiver, provider, or class as a plugin.
VirtualAPK can test a huge arsenal of native Android features in a large range of Android versions (from API 15+) and devices.
Xposed Framework
The Xposed Framework makes it easy to perform dynamic analysis of your app using Android hooking. It is by far one of the most popular hooking frameworks available to the Android community.
It gives you the power to change the functionality of the OS or any app in any way you want. It also lets you create add-ons (popularly known as modules) that can hook into any method and change its functionality, allowing you to analyze and test any app at runtime.
Build it secure from the start
I hope you will find some of these tools useful for discovering vulnerabilities and tightening the security of your Android apps. Take some time to explore and learn these tools and you can build apps that are secure from the outset.
If you have other tools you'd recommend for improving the security of Android applications, please share them in the comments.
Keep learning
Take a deep dive into the state of quality with TechBeacon's Guide. Plus: Download the free World Quality Report 2022-23.
Put performance engineering into practice with these top 10 performance engineering techniques that work.
Find to tools you need with TechBeacon's Buyer's Guide for Selecting Software Test Automation Tools.
Discover best practices for reducing software defects with TechBeacon's Guide.
- Take your testing career to the next level. TechBeacon's Careers Topic Center provides expert advice to prepare you for your next move.